Managing Salesforce Permissions is one of the most crucial skills every admin, consultant, or developer needs to master. It ensures that the right people have access to the right data. But with Profiles, Roles, and Permission Sets all working together, it can get confusing quickly. In this blog, we’ll break down these key access tools clearly and simply. Whether you’re new to Salesforce or looking to fine-tune your setup, this guide will help you understand how to manage user access effectively and securely within your Salesforce org.
Understanding the Foundation: Profiles
Think of Profiles as the foundational blueprint for user access in Salesforce. They define the “what” a user can do within the system. Every Salesforce user is assigned one, and only one, profile. Profiles control a wide range of settings, including:
- Object Permissions: Granting the ability to create, read, edit, delete, and view all data for specific standard and custom objects (CRUD permissions).
- Field-Level Security (FLS): Controlling whether a user can view and/or edit specific fields on an object.
- App Permissions: Determining which Salesforce applications a user can access.
- System Permissions: Granting access to system-level functionalities, such as managing users, customizing the application, and running reports.
- Tab Settings: Defining which tabs are visible to the user.
- Record Type Settings: Specifying which record types are available to the user for specific objects.
- Page Layout Assignments: Determining which page layouts users see for different record types.
Key Takeaways about Profiles:
- Mandatory: Every user must have a profile.
- Broad Control: Profiles govern a wide array of functional access.
- Assigned Once: Each user is assigned only one profile.
- Base Functionality: They establish the fundamental capabilities of a user.
Adding Granularity: Roles
While profiles define what a user can do, Roles focus on what data a user can see based on their position within the organizational hierarchy. Roles are optional but highly recommended for managing data visibility. The Salesforce Role Hierarchy enables record access based on a user’s position relative to others.
Imagine a sales team with a VP of Sales, Regional Sales Managers, and Sales Representatives. The Role Hierarchy can be structured to ensure:
- The VP of Sales can see all sales data.
- Regional Sales Managers can see data owned by users in their respective regions and those below them in the hierarchy.
- Sales Representatives can typically see only the data they own.
Key Takeaways about Roles:
- Optional: Users can be assigned a role, but it’s not mandatory.
- Data Visibility: Primarily controls data access based on hierarchy.
- Hierarchical Structure: Organizes users in a tree-like structure.
- Record Ownership: Access is often granted to records owned by users in subordinate roles.
- Sharing Rules: Roles work in conjunction with sharing rules to refine data access further.
Extending Access: Permission Sets
Permission Sets offer an effective means to extend user permissions beyond those granted by their profile. Think of them as add-on packages that enhance a user’s capabilities without requiring the creation of multiple profiles. This is particularly useful for granting specific, temporary, or role-based access to a subset of users.
Permission Sets can contain any of the settings found in a profile, such as object permissions, field-level security, app permissions, and system permissions.
Key Takeaways about Permission Sets:
- Optional: This can be assigned to users as needed.
- Granular Access: Provides specific permissions without altering the base profile.
- Flexible: Can be assigned to multiple users and multiple permission sets can be assigned to a single user.
- Efficiency: Reduces the need for profile proliferation.
- Temporary Access: Ideal for granting temporary access to projects or tasks.
Putting It All Together: A Practical Approach
The most effective Salesforce permission strategy involves a thoughtful combination of profiles, roles, and permission sets:
- Start with Profiles: Define base-level access for different types of users (e.g., Sales User, Marketing User, Support Agent). These profiles should represent the minimum necessary access for each user type.
- Implement Roles: Establish a clear Role Hierarchy that reflects your organizational structure to manage data visibility effectively. This ensures users can access the relevant data based on their position.
- Utilize Permission Sets: Extend access for specific users or groups who require additional functionalities beyond their profile. This could include granting a Sales Representative the ability to manage campaigns for a project or allowing a Support Agent to access advanced diagnostic tools temporarily.
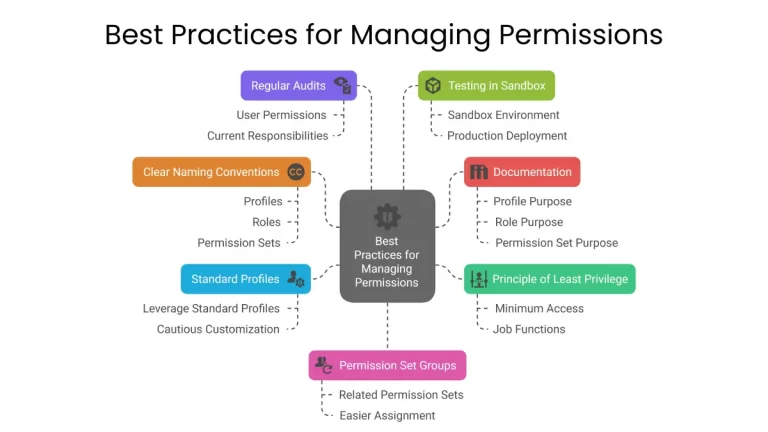
Best Practices for Mastering Salesforce Permissions
- Principle of Least Privilege: Grant users only the minimum level of access required to perform their job functions.
- Standard Profiles: Leverage standard profiles whenever possible and customize them cautiously.
- Clear Naming Conventions: Choose clear and descriptive names for profiles, roles, and permission sets to make their purposes easily recognizable.
- Regular Audits: Periodically review user permissions to ensure they remain appropriate and aligned with their current responsibilities.
- Documentation: Maintain clear documentation of your permission strategy, including the purpose of each profile, role, and permission set.
- Testing in Sandbox: Always test permission changes in a sandbox environment before deploying them to production.
- Consider Permission Set Groups: For organizations with many permission sets, leverage Permission Set Groups to bundle related permission sets for easier assignment and management.
Final Thoughts
Mastering the Salesforce permission model is a crucial step in your Salesforce journey. Improving security and efficiency in Salesforce requires tackling common problems with Profiles, Roles, and Permission Sets, such as misconfigurations and excessive access. Regular audits, aligning roles with the organizational structure, and adhering to the principle of least privilege can improve governance and ensure proper access control.
Must Visit Links:
- How to Crack the Salesforce Interview: Real Questions and Tips from Experts
- How Much You Can Earn as a Salesforce Consultant in 2025?
- Top Most In-Demand Salesforce Skills for 2025: What Professionals Need to Know
- The Importance of Hands-On Experience in Mastering Salesforce Skills
- How I Passed the Salesforce Data Architect Exam on My First Attempt
- How to Prepare for the Certified Agentforce Specialist Certification Exam
Resources
- [Salesforce Developer]- (https://developer.salesforce.com/)
- [Salesforce Success Community] (https://success.salesforce.com/)
For more insights, trends, and news related to Salesforce, stay tuned with Salesforce Trail
Mark Jacobes is a seasoned Salesforce expert, passionate about empowering businesses through innovative CRM solutions. With over 6 years of experience in the Salesforce ecosystem, Mark specializes in Salesforce development, integrations, and digital transformation strategies.
- Mark Jacobeshttps://salesforcetrail.com/author/markjacobes/September 8, 2025
- Mark Jacobeshttps://salesforcetrail.com/author/markjacobes/
- Mark Jacobeshttps://salesforcetrail.com/author/markjacobes/
- Mark Jacobeshttps://salesforcetrail.com/author/markjacobes/













